SaaS overview
In addition to on-premises deployments, Instabase is available as a software as a service (SaaS) installation. An SaaS installation offers a convenient and secure way to use the Instabase platform and access the latest innovations and breakthroughs in AI-led functionality.
If you’re interested in becoming a SaaS customer, reach out to your Instabase account manager.
Advantages
Advantages to accessing the Instabase platform through a SaaS installation rather than an on-premises one include:
-
Access to the entire Instabase platform without needing to procure, configure, and manage complex infrastructure.
-
A faster time to business value, with less time spent on infrastructure setup and management leading to more time to spend on solution development.
-
The ability to scale easily with no overhead as automation demands increase.
-
Your platform infrastructure is automatically kept up-to-date as Instabase releases are made available.
Architecture
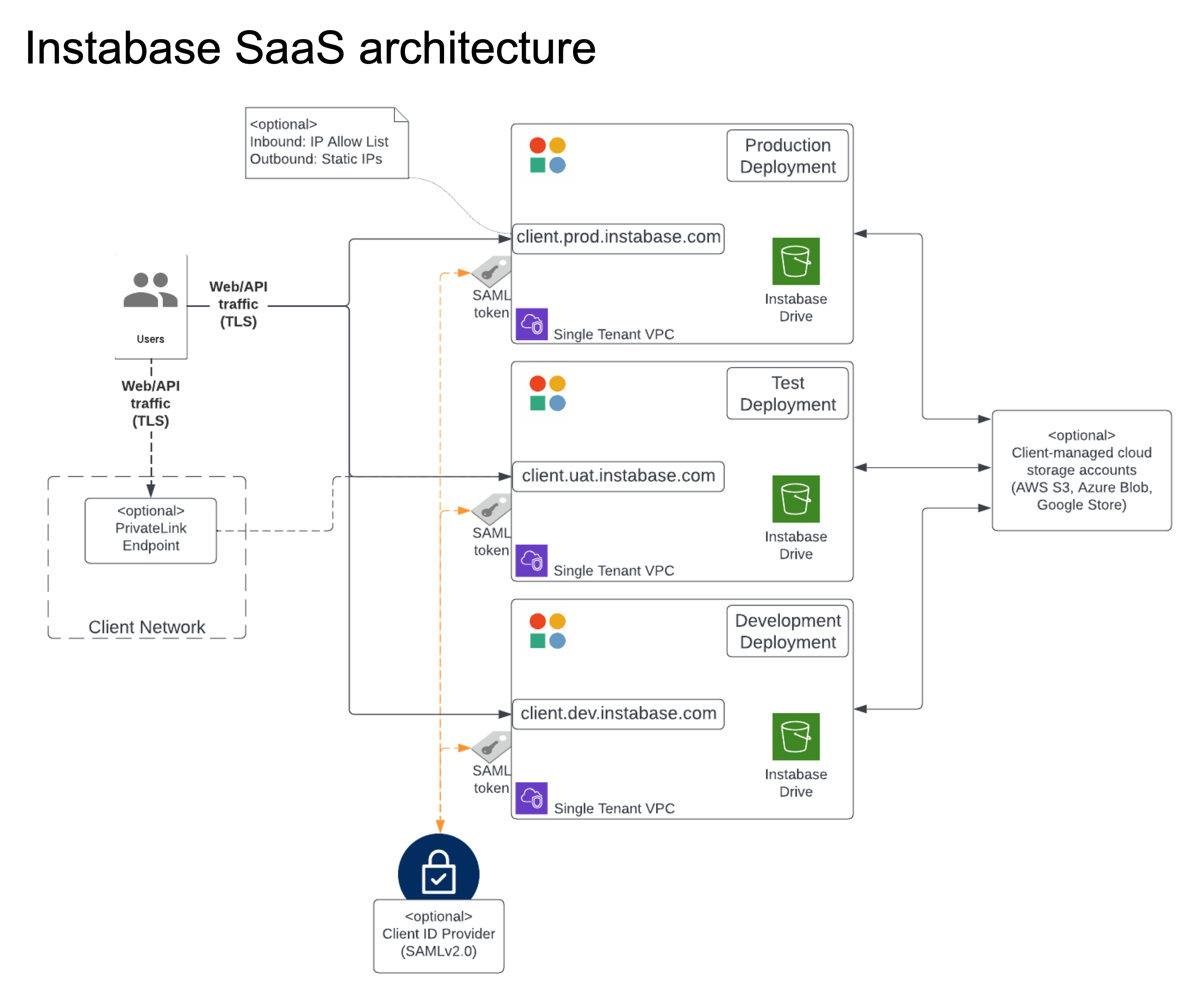
Every SaaS customer receives their own customer installation. A customer installation comprises up to three deployments: development (DEV), user acceptance testing (UAT), and production (PROD). Each deployment in the installation is hosted in the Instabase Amazon Web Services (AWS) account and is self-contained, network-isolated, and complete.
The following diagram provides a more detailed look at the architecture of a SaaS installation:
For all SaaS installations, Instabase is responsible for the infrastructure, deployment, management, and ongoing monitoring of the platform. An installation also has several optional integrations for identity, client storage accounts, front-end access, and back-end service access to meet your integration needs.
Support and availability
The PROD deployment of your customer installation is available with minimum service availability and guaranteed uptime, excluding scheduled downtime and exclusions. To ensure this minimum availability, Instabase continuously monitors the health of each customer installation and has operational procedures in place to identify and resolve any issues that could occur within each deployment that might result in downtime or degraded performance.
As a SaaS customer, you have access to the Instabase Cloud Console, where you can view the status of each deployment in your installation, including component-specific statuses at any time. If you encounter any downtime or issues, you can submit a support ticket through Zendesk. Support tickets are responded to and triaged based on severity.
Security and privacy
Instabase maintains a risk-based assessment security program. The framework for Instabase’s security program includes administrative, organizational, technical, and physical safeguards designed to reasonably protect all services, in addition to the confidentiality, integrity, and availability of customer data.
Practices
Instabase has separate and dedicated Information Security teams that manage Instabase’s security program. This includes a team that facilitates and supports independent audits and assessments performed by third parties. Instabase’s security framework is based on the AICPA’s Trust Services Criteria (security, confidentiality, and availability) and industry best practices.
Areas our security program covers include:
-
Policies and procedures
-
Asset management
-
Access management
-
Cryptography
-
Physical, operations, and communications security
-
Business continuity disaster recovery security
-
People and product security
-
Cloud and network infrastructure security
-
Security compliance
-
Third-party security
-
Vulnerability management
-
Security monitoring and incident response
Information security policies and standards are reviewed and approved by management at least annually to keep pace with changes in regulations, technologies, and industry best practices. Information security policies are made available to all Instabase employees for their reference.
Validations
The Instabase SaaS platform is SOC 2 Type II certified and designed to be compliant with GDPR, HIPAA, and CCPA. To review our compliance reports and learn more about our additional security measures, visit the Instabase Trust Center.
Vulnerability management
Instabase conducts automated daily security assessments for early detection and remediation of vulnerabilities. Vulnerabilities are remediated by applying patches, making code or infrastructure changes, or through other procedural means as needed. All vulnerabilities are categorized based on criticality and resolution timelines are established based on severity. You can request access to the Instabase vulnerability management policy from your customer success manager.
Penetration testing
Instabase performs penetration tests and engages independent third-party entities to conduct application-level penetration tests. Security threats and vulnerabilities that are detected are prioritized, triaged, and remediated promptly. If applicable under the terms of your NDA, you can request executive summaries of penetration test reports. These reports include test results as well as any measures taken to address any concerns that were discovered.
Data access
By default, Instabase does not have direct, frontend access to any customer installation. If you require support or assistance from Instabase, you can either request a screen-sharing session or provision an Instabase employee with access through your chosen user authentication method.
Instabase employees can directly access the infrastructure of SaaS installations only under very specific circumstances, such as when an emergency break-fix is required. All activities of Instabase employees at both the platform and infrastructure level are logged and auditable.
Data security
Instabase utilizes encryption at various points to protect your data and secrets. We encrypt data at rest using the industry-standard AES-256 encryption algorithm for data stored within each deployment. We protect secrets such as passwords and access tokens using industry-standard key management systems, secrets managers, or encryption within the dedicated database. In addition, when using Amazon S3 storage, Azure Blob Storage, or Google Cloud Storage, data is encrypted in-transit through encrypted network channels (TLS/HTTPS) for all client/server communication.
Limitations
While using Instabase through a SaaS deployment offers several advantages compared to an on-premises deployment, there are some limitations to be aware of:
- You can’t add additional third-party libraries beyond the default set of third-party libraries.